Security Issues in Cloud Computing

DOI:
https://doi.org/10.54060/JMSS/002.01.003Keywords:
Cloud computing, Models, Threats, CountermeasuresAbstract
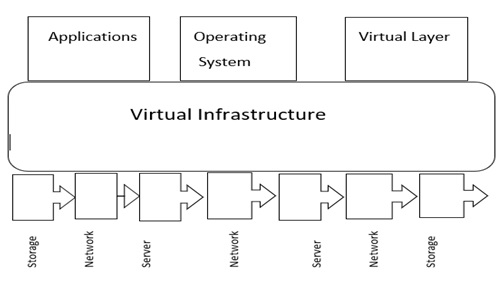
Cloud computing has aided the evolution of IT by improving the ability and flexibility of data storage, as well as providing scalable computation and processing capabilities that match the dynamic data sets. Many corporate application programs have been transferred to public and hybrid clouds due to the multiple benefits of cloud computing. On the other hand, many businesses identify privacy and data security as major concerns that prevent them from adopting cloud computing. The only way to achieve successful cloud implementation is to improve and manage data security and privacy in the cloud. This research paper looks at data privacy and security in cloud computing at all stages of the data lifecycle, providing a general overview of the technology while highlighting important security difficulties and concerns that must be addressed. It also examines a number of existing solutions and gives recommendations for new ones that can improve data privacy and security in the cloud. Finally, future research on data privacy and security in cloud systems is discussed in the study report.
Downloads
References
M. K. Sasubilli and Venkateswarlu, “Cloud computing security challenges, threats and vulnerabilities,” in 6th International Conference on Inventive Computation Technologies (ICICT), 2021.
K. Hashizume, D. G. Rosado, E. F. Medina, et al, “An analysis of security issues for cloud computing,” J. Internet Serv. Appl., vol.4, no.1, pp. 5, Feb 2013.
R. Mogull, J. Arlen, F. Gilbert, et al,” Security guidance for critical areas of focus in cloud computing v4.0”, Cloud Security Analysis Research Publications. https://cloudsecurityalliance.org/download/security-guidance-v4/, July 2017.
YumpuePPER,”cloudcomputingInformationSecurityBriefing,01/2010CPNI,”.https://www.yumpu.com/en/document/view/35595642/cloud-computing-information-security-briefing-01-2010-cpni, Jan 2015.
Top threats,” Cloudsecurityalliance.org. [Online]. Available: https://cloudsecurityalliance.org/research/top-threats. [Accessed: 21-Jul-2022].
OWASP: The Ten most critical Web application Security risks. https://www.owasp.org/index.php/Category:OWASP_Top_Ten_Project
IBM. (n.d.). Identity Mixer. Retrieved from www.zurich.ibm.com/security/idemix/
International Telecommunication Union, “Distributed Commuting: Utilities, Grid & Clouds”. https://www.itu.int/dms_pub/itu-t/oth/23/01/T23010000090001PDFE.pdf “March 2009.
P. Mell & T. Grance, “NIST Definition of Cloud Computing,” Retrieved from ver.15,” Computer Security Resources Center NIST” www.nist.gov/itl/cloud/upload/cloud-def-v15.pdf ,July 2009.
S. Kamara and K. Lauter, “Cryptographic Cloud Storage,” in Financial Cryptography and Data Security, Berlin, Heidelberg: Springer Berlin Heidelberg, LNCS, vol.6054, pp. 136–149,2010.
J. Horrigan, Use of Cloud Computing Applications and Services, Pew Research Center: Internet, Science & Tech. https://policycommons.net/artifacts/626957/use-of-cloud-computing-applications-and-services/1608265/ on 21 Jul 2022.
A. R. Lombarte “Madrid Resolution, International Standards on the Protection of Personal Data and Privacy”,” International Conference of Data Protection and Privacy Commissioners, “pp.1-36, Nov 2009.