Cryptography: Security and Integrity of Data Management

DOI:
https://doi.org/10.54060/JMSS/001.02.004Keywords:
Data Encryption and Decryption, Compression, Cryptography Concepts, Security, IntegrityAbstract
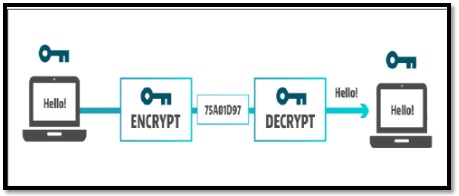
Internet always deals with data. Basically, data is any type of digital information that has been stored in the servers. With the advancement of technology, billion tons of data have been accumulated over the internet. Protection of these data is very crucial as; theft of these data will lead to damages beyond imagination. Data Security is protection of these data and privacy, which prevent hacker from unauthorized access to computers, applications, and data servers. Data security is achieved by implementing Cryptography. Cryptography is a technique in which data is encrypted and stored in the databases, so that if by chance anyone gets access to these data, it will of no use to them. There are many cryptography algorithms that are widely used to encrypt and decrypt data, some of them are AES algorithm, stream ciphers, DES algorithms, etc. The concept of cryptography is not only limited to text encryption but also it has a wide application in visual cryptography, watermarking, steganography, etc. Now a day’s security of communication has become very important, especially after people have started using internet banking. Everything on world wide web is all about confidentiality, integrity, and authentication.
Downloads
References
T. Zhou, J. Shen, X. Li, et al, “Quantum cryptography for the future Internet and the security analysis,” Secur. Commun. Netw., vol. 2018, pp. 1–7, 2018.
A. K. Ekert, “Quantum cryptography based on Bell’s theorem,” Phys. Rev. Lett., vol. 67, no. 6, pp. 661–663, 1991.
A.K. Ekert, “Centre for Quantum Computation -Oxford University,” Commun. ACM, vol. 38.
R. Colin Johnson, "MagiQ employs quantum technology for secure encryption." EE Times, 11 May 2002.
J. Mullins. "Quantum Cryptography's Reach Extended." IEEE Spectrum Online. 1 Aug. 2003.
N. Jirwan, A. Singh, and S. Vijay, "Review and Analysis of Cryptography Techniques," International Journal of Scientific & Engineering Research, vol. 4, no. 3, pp. 1-6, March 2013.
S. Tayal, N. Gupta, P. Gupta, et al, "A Review paper on Network Security and Cryptography," Advances in Computational Sciences and Technology vol. 10, no. 5 pp. 763-770, 2017.
J. Callas, “The future of cryptography,” Inf. Syst. Secur., vol. 16, no. 1, pp. 15–22, 2007.
J. L. Massey, "Cryptography—A selective survey," Digital Communications, vol. 85, pp. 3-25, 1986.
B. Schneier, “The nonsecurity of secrecy,” Commun. ACM, vol. 47, no. 10, 2004.
N. Varol, A. F. Aydogan, and A. Varol, “Cyberattacks targeting Android cellphones,” in 5th International Symposium on Digital Forensic and Security (ISDFS), 2017.
S. Yadav and P. Singh, “Web Application and Penetration Testing,” Journal of Informatics Electrical and Electronics Engineering, vol. 1, no. 2, pp. 1–11, 2020.
S. K. Tomar and P. Singh, “Cyber Security Methodologies and Attacks,” Journal of Management and Service Science, vol. 1, no. 1, pp. 1–8, 2021.